10 Powerful Microsoft 365 Security Actions to Take Now
This blog post dives into 10 powerful Microsoft 365 security actions your business needs to take action on now!
Small to medium sized businesses are not exempt from cyberattacks in todays world. The actions in this blog post will increase your business security and help reduce your cybersecurity risk.
To get a benchmark of the security within your Microsoft 365 environment otherwise known as a tenant. More than likely, your Microsoft 365 security settings will look like the image below. Check out Microsoft 365 Secure Score from a centralized dashboard, as you increase the security in your tenant the security score will improve for identities, data, apps, devices and infrastructure.
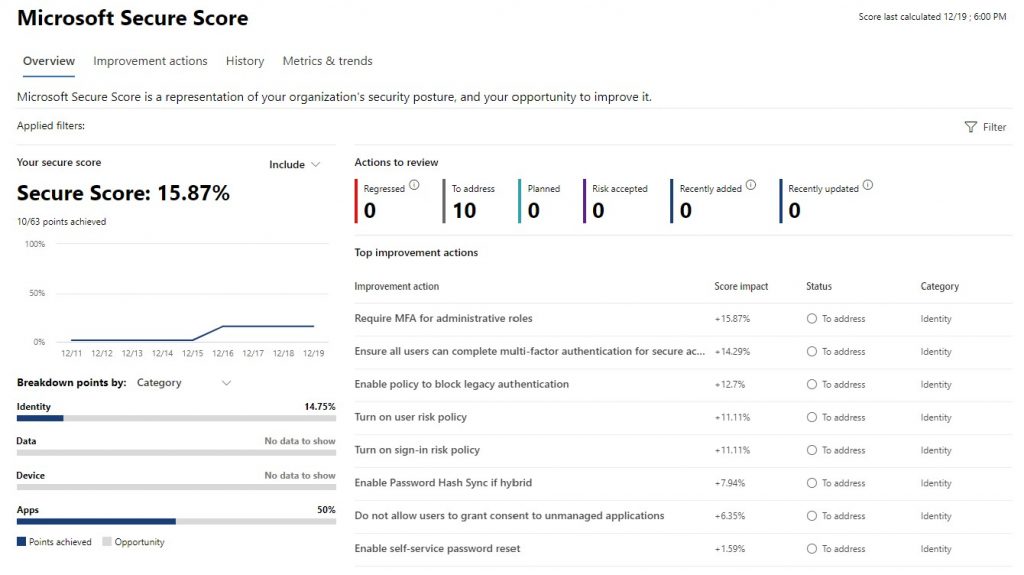
Ten Actions – Microsoft 365 Security
Multi-Factor Authentication
Using multi-factor authentication (MFA) built into Microsoft 365 Business Premium is an easy and effective way to increase the security for your organization. Check this video out to activate the feature now by turning on security defaults.
Security defaults include MFA, for new tenants this may automatically be turned on. In order to enable or disable security defaults, follow this process.
- Sign into Microsoft 365 Admin Center with global admin credentials.
- In the left navigation select Show All and under Admin Centers, select Azure Active Directory.
- In the Azure Active Directory admin center select Azure Active Directory -> Properties.
- At the bottom of the page, select Manage Security defaults.
- Select Yes to enable security defaults or No to disable security defaults, and then select Save.
Once MFA is activated, the users within your organization will be required to setup two-step verification on their devices. This video will walk you through that process.
Train your users
Employees are the weakest link. If you want to get the biggest return on investment, create online awareness training videos with your employees. Sure, you can buy courses from other people, but you will get a greater value involving your employees.
Harvard Kennedy School put together a great Cybersecurity Campaign Handbook that provides a great place to start.
Use Dedicated Admin Accounts
Administrative accounts in the Microsoft 365 environment contain elevated privileges. Cyber criminals seek and desire to get a hold of these accounts to exploit and attack the environment. If your normal day to day account is the administrative account, your compromised account just let the hacker take over.
Here are five (5) recommendations:
- Normal day to day accounts should not be administrative accounts
- Only use an administrative account when necessary
- Admin accounts need to be set up for multi-factor authentication
- Before using admin account close out all unrelated browser sessions and apps, including personal email accounts
- After completing admin tasks, be sure to log out of the browser session
Raise the Level of Protection
The Microsoft 365 environment includes protection against malware which can be increased by blocking attachments with certain file types. To increase the protection, follow these steps:
- Go to https://protection.office.com/ and sign in with your admin account credentials
- In the Office 365 Security & Compliance Center left navigation pane, under Threat management -> choose Policy -> select Anti-Malware
- Double-click the default policy to edit this company-wide policy
- Select Edit policy
- On the left side, select Common attachment types filter, make sure this is On. The file types that are blocked will be listed under Selected attachment type.
- If you want to add more or take some away, select Choose type.
- Click on Save
Protect against Ransomware
Implement the following two mail flow rules which will help reduce the ransomware threat to your business:
- Warn users before opening Office file attachments that include macros. Ransomware can be hidden inside macros, so warn users not to open these files from people they don’t know.
- Block file types that contain ransomware or other malicious code. Start with a common list of executables.
Stop Auto-forwarding for Email
Create a mail transport rule to stop external automated email forwarding. Most of the time Hackers who gain access into a Microsoft 365 environment will automatically forward emails out to monitor the inbox without the user knowing. They look for a financial transaction that can be compromised.
Use Office Message Encryption
Your Microsoft 365 tenant already contains the ability to send and receive encrypted email messages both inside and outside of your business. From within Outlook for PC, select Options in the email, and then choose Permissions as shown below.
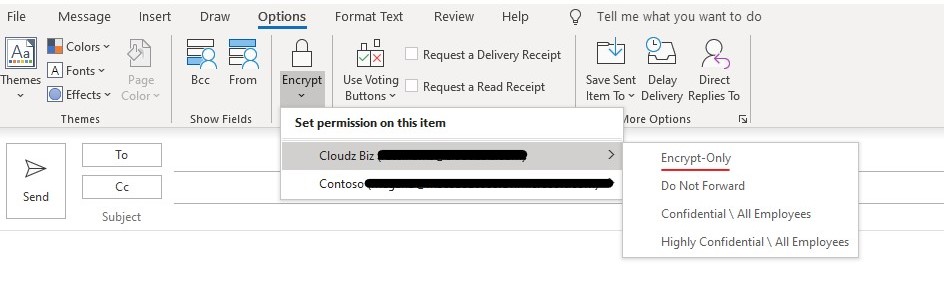
Protect your email from phishing attacks
Microsoft 365 Business Premium allows you to enhance anti-phishing protection for one or more customer domains tied to your tenant. This feature is part of Microsoft Defender for Office 365 and protects your organization from malicious impersonation-based phishing attacks and other phishing attacks.
Protect against malicious attachments and files
Organizations regularly send, receive, and share attachments in day to day business transactions. These attachments contain documents, presentations, spreadsheets, and more. It’s not always easy to tell whether an attachment is safe or malicious just by looking at an email message.
Microsoft Defender for Office 365 includes Safe Attachment protection, but this protection is not turned on by default. We recommend that you create a new rule to begin using this protection.
Protect against phishing attacks with Safe Links
Microsoft 365 Business Premium provides the ability to protect against malicious websites hidden within links in emails or other files. You can find this feature within the Office 365 Security & Compliance environment under Threat management. Define the protection through Safe Links policies.
Microsoft 365 Security Summary
If you are looking for more information, check out another blog 7 Keys for Small Business Cloud Technology Success. Also, this link as well provides more information on the recommendations from this blog.
As we mentioned above, a great resource to reference for cybersecurity direction is the Harvard Kennedy School Cybersecurity Campaign Handbook.
Most businesses won’t take advantage of this offer. Free 30 minutes consulting if you need help implementing the above features in your tenant. Use the link to schedule a session.


Recent Comments